When a hacker is able to obtain access to a user’s cryptocurrency account, 99.9% of the time it’s due to a breach of user’s seed phrase. But the seed phrase can be breached in a variety of ways, allowing a hacker to steal cryptocurrency, and there are different attack vectors available depending on how a user elects to store it, all with their own vulnerabilities.
In this article, we provide a comprehensive guide that details the vulnerabilities and attack vectors hackers utilize to steal Bitcoin and cryptocurrencies. It does not include all ways that may cause a victim to lose funds such as ways an attacker might utilize to get a victim to send funds under false pretenses, such as in an impersonation scam for example. These are covered in our Comprehensive Guide to Cryptocurrency Frauds and Scams – arguably, it’s actually a fair bit more common to be defrauded or scammed out of cryptocurrency than it is to be hacked and to have one’s funds outright stolen, so keep that in mind. However, this guide only covers ways whereby the attacker is able to steal and send funds from a wallet which the victim also controls without their consent.
While users will never be able to ensure with certainty that their wallet or funds will never be breached, by embracing and understanding vulnerabilities and attack vectors hackers utilize to steal Bitcoin and other cryptocurrencies, one can drastically reduce the risk of becoming compromised. Given the number of investigations we’ve conducted into such thefts and hacking incidents, we feel we’re in an optimal position to help warn the public about the ways in which their funds are vulnerable to being compromised, so they can take action accordingly.
Cloud Storage Breach
In the vast majority of cryptocurrency thefts, a breach of the victim’s cloud storage is almost always involved. This cloud storage includes Email, Google Drive, Dropbox, iCloud, Google Photos, Microsoft OneDrive, and Yahoo accounts. Simply put, many people end up storing their seed phrase on the cloud which ends up getting breached.
This is statistically the most common breach vector and can lead to the breach of any type of cryptocurrency wallet; software wallets, hardware wallets, mobile wallets, or paper wallets (which of course aren’t paper wallets anymore once a copy of the seed phrase is stored digitally). Sometimes people store their seed phrase on the cloud inadvertently, by taking a photo of their seed phrase, not realizing those photos are backed up to the cloud which hackers look for.
Even when a victim hasn’t stored their seed phrase on email or cloud storage, it’s still common for a breach of the victim’s email to be involved. This is because once a hacker has control of a victim’s email, they have control over a lot of other things, including the ability to reset passwords in addition to seeing all the places the user has accounts based on old emails. There are a variety of methods hackers employ to breach the email and cloud storage accounts, to begin with.
Password Breach
Historically, the most common is a simple password breach. This can be caused by an easy-to-guess password, but can also be caused by password reuse. When a username or email and password combination is found to be associated with a given service or website, hackers try to use this email and/or username out on other platforms they know or believe the victim may use. Re-use of passwords here is a recipe for disaster. Data from these breaches are often quickly included in breach databases and is available to any (nefarious) actor willing to pay. A good way of determining whether your email has been included in a known database breach is by going to the website HaveIBeenPwned.
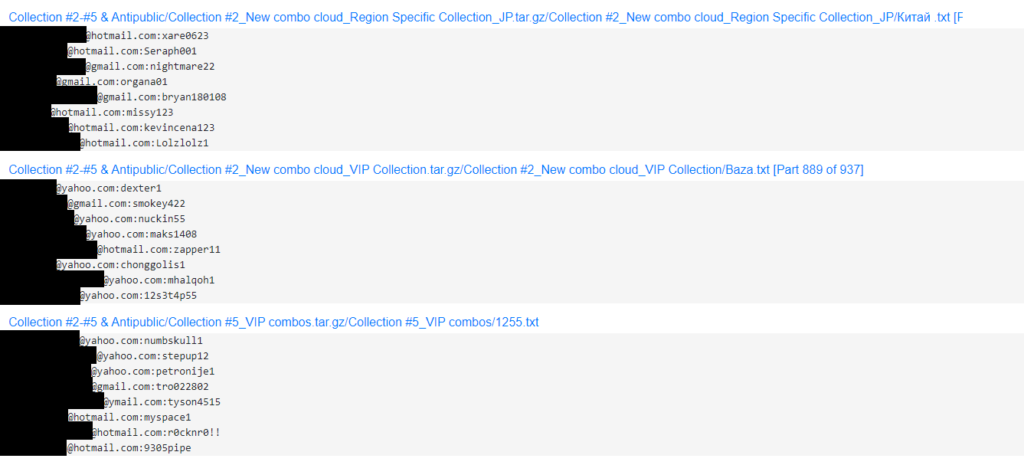
These databases are both plentiful and easily accessible if you know where to look.
SIM Swap
Some people have started to realize that even if a password itself is ‘secure’ it’s still not safe. A second authentication factor is needed to prevent unauthorized access to an account because password breaches are so common, and malware can easily compromise one’s password as well. This leads many people to utilize their phone number (and SMS) as a second authentication factor, hence ‘SMS 2FA’.
What some still don’t realize is that SMS 2FA is extremely vulnerable in particular to a SIM Swap and thus should never be used as a form of 2FA, despite widespread usage. As explained in the SIM Swapping Bible, a SIM Swap or SIM Jack is where an attacker ports a victim’s phone number over to a SIM they control. It’s not overly difficult for a hacker to do and it happens all the time.
Once the phone number has been ported, the hacker starts to receive the 2FA messages on their phone. This can offer them easy access to the account if they already have the password. However, even if they don’t know the password in many cases they are able to use the phone number to reset the password since they obviously don’t have access to the email account they’re trying to log into. Once the email account has been breached, the hacker has access to the victim’s email account and has 2FA access both for the email and elsewhere.
Furthermore, if you use Authy as a form of app-based 2FA, you should know that the Authy app itself is vulnerable to a SIM Swap attack if not set up correctly as we’ve noted in the SIM Swapping Bible. I know, that kind of defeats the point of app-based 2FA to begin with, right? It’s definitely poor design on Authy’s part, but provided that the Authy app is set up the way we’ve indicated, you won’t be vulnerable to a SIM Swapping attack. Alternatively, consider Google Authenticator or purchasing a Yubikey.
Backup Email
Another way a victim’s email account is breached (which can easily lead to cryptocurrency theft) is through a backup email. People often have an old or backup email address they utilize occasionally or almost never in some cases. However, this backup email is listed as the recovery email for their main email. The backup email typically employs very poor security since the victim doesn’t really use the email much, if at all. However, a breach of the backup email allows a hacker to breach the main email account quite easily via a ‘password recovery’.
Malware
Malware comes in many forms and is one of the more common breach vectors. Let’s take a look at some of the most common malware that can cause cryptocurrency theft:
Keyloggers
A keylogger records keystrokes which may include the entering of passwords or entering seed phrases directly. Mass Logger is but one example here. For obvious reasons, this can easily result in one’s cryptocurrency being stolen. The solution here, as you’ll find all the other forms of malware is fairly simple; use a hardware wallet! That being said, while a hardware wallet will help protect you against being compromised due to malware, it won’t be of any help if the seed phrases aren’t stored securely.
Clipboard Hijacking
There are multiple forms of clipboard hijacking malware available. This includes malware that tracks what is copied to the clipboard, which of course can include a seed phrase, private key, or longer passwords. In many ways this type of malware functions fairly similar to the keylogger.
Then there are separate types of clipboard hijackers that covertly change what is on a victim’s clipboard. Specifically, when this malware detects a victim has copied a Bitcoin or other cryptocurrency address to the clipboard (where the victim obviously may intend on sending funds there), it covertly replaces that address with an address controlled by the hacker. The victim then sends funds to the address, thinking they’ve sent funds as intended when in reality, the malware caused them to send funds directly to the hacker.
Browser Extension Exploits
A considerable portion of malware that gets on people’s computers are through malicious or compromised browser extensions. Hackers are sometimes able to exploit vulnerabilities in existing extensions people install. Adobe Flash has historically been an extremely common extension to exploit, but there are plenty of others. Other extensions have been found to be malicious to begin with.
Compromised Wallet Software
Hackers sometimes make small modifications to existing wallet software, and then redistribute this release, under the guise of it being an ‘official’ release. Unbeknownst to the victims, this wallet software is malicious and the hacker can steal a victim’s funds once the compromised wallet software is accessed by the victim.
The way to avoid inadvertently downloading a compromised wallet is by downloading the software from the official source (be sure you’re not on a phishing URL) and then verifying the digital signature of the software against the signature found on the website’s download page.
Fake Wallets and Applications
Separate from the compromised wallet software are two other types of malicious wallet software. There’s imitation wallet software that hasn’t been modified but nonetheless appears quite similar to existing software. Ledger’s, ‘Ledger Live’ is a frequent target here, with malicious copycats everywhere.
Then there is non-imitation wallet software that isn’t really a wallet at all – just a way to get users to enter their seed phrases. These wallets in particular aren’t using the names of legitimate wallet software but using their own ‘brand’.
Screen Capture Malware
Similar to the keyloggers and clipboard malware, there is also screen recording malware that captures a victim’s computer screen and uploads it to a server that the hacker then accesses, which could give away passwords, seed phrases, private keys, and other personally identifying information that can easily lead to one’s funds being stolen or accounts being compromised.
Offline Digital Seed Phrase Compromise
Some people assume that it’s safe to store their seed phrase on digital devices so long as it stays offline. However, seed phrases stored offline can be compromised as well. Furthermore, sometimes although people believe they’ve only stored their seed phrase offline, they’ve actually stored it online on the cloud. Google photos are but one example here, as these photos are automatically backed up to a person’s Google account. In other cases, people do store their seed phrase in a text or word file offline, which can be compromised via two main avenues.
First is a breach of the device itself. Laptops are sometimes stolen, as are phones, and if an attacker is able to access a victim’s account on these devices and knows a victim stores cryptocurrency on them, it wouldn’t be difficult for a thief to find the backup. One should also be cognizant of the possibility of a friend or family member stealing the funds since they would have much easier access to one’s electronic devices in most cases.
The second is malware. Malware comes in many different forms as previously mentioned including those that search for and upload a victim’s data to a server without their consent, to malware that tracks usage of the clipboard function, to screen-recording malware. Malware is highly effective at stealing funds when seed phrases are stored in plaintext on a digital device, even if stored offline.
Physical Theft of the Paper Seed Phrase
Physical theft of the paper seed phrase is a concern most cryptocurrency users are aware of. However, relative to the other breach vectors discussed here, it’s actually fairly uncommon to lose funds via this method. When funds are stolen due to an unauthorized party accessing a physical paper copy of the seed phrase, it’s most often an internal theft by a close friend or family member, rather than a burglar unknown to the victim.
When setting up almost any cryptocurrency wallet for the first time, it’s likely to state ‘write this seed phrase down on paper and do not store on any digital device’ or something similar to this. This is because theft of the paper seed phrase is relatively rare and not something any online hacker would be able to access.
Nonetheless, one should still be mindful of how and where they store the paper seed phrase. A wall safe is the optimal solution, preferably one that’s hidden, but that’s obviously not something everyone has access to. A bank lockbox is a good alternative, but that doesn’t provide as easy of access as having the seed phrase at one’s house. Furthermore, if an individual has a particularly large amount of cryptocurrency, they may not want to trust that the bank.
In the absence of proper equipment to secure a paper seed phrase, one should at least strive to store their seed phrase in a place that isn’t obvious but also won’t accidentally be stumbled upon by another family member or accidentally thrown out. A good idea that would meet these criteria would be inside a locked filing cabinet inside an old tax return folder. No one in their right mind would ever dare to look in there unless you disclosed it.
Phishing
Phishing comes in many different forms. They include fake exchange websites that steal one’s password, fake wallets, fake exchange websites that look practically identical to the real thing and have an almost identical URL, as shown in the Bittrex example below.

Look closely at the URL
The applications and websites discreetly steal a user’s credentials, thereby allowing a hacker to access a user’s account themselves.
These phishing links are posted by the hacker (or those they hire) all over to the place, to include, Reddit, Quora, blog articles, Facebook groups, Telegram groups, and they even pay to place such phishing links as Google Ads in some cases, making it appear as the top result.
Trusting Another Party
Some people elect to trust close friends, family members, and business partners with their cryptocurrency or the ability to access their cryptocurrency if needed, such as in the event of death or incapacitation. Occasionally, Cryptoforensic Investigators sees people betray that trust which in turn causes further issues with relationships the victim has with others.
While this isn’t overly common, one needs to take the amount of cryptocurrency assets into context when assessing the risk of such an event occurring. It’s much less likely for a close friend to try and steal $10,000 worth of cryptocurrency than it is for a close friend to steal $10,000,000 worth of cryptocurrency.
While a notary is generally considered quite safe for such purposes, depending on the amount of cryptocurrency wealth involved, one could reasonably even want to avoid trusting the notary entirely. In such cases, a 2 of 3 multi-sig is generally the best option. This is actually a setup we employ as part of our cryptocurrency inheritance and estate planning for high net worth clients, the trusted parties being a close friend of the beneficial owner of the funds (e.g. power of attorney), a notary or lawyer chosen by the beneficial owner, and Cryptoforensic Investigators.
Exchange Hacks
Those who elect to store cryptocurrency on an exchange are also at risk of having their funds on exchange hacked. There are two types of exchange hacks we first want to differentiate between; exchange account hacks and exchange reserves or storage hacks.
Exchange Account Hacks
An exchange account hack is when a specific user’s account on a cryptocurrency exchange is targeted. These are considerably more common than attacks that attack the exchange as a whole. Exchange account hacks involve breaching and gaining access to a specific account, and then withdrawing whatever balance is held on the account. In some cases, this can be in the millions of dollars, depending on how much cryptocurrency the victim stores ‘on exchange’.
One reason exchange accounts are sometimes breached is due to password breach. The likelihood of a password breach is increased when an easy-to-guess password is used and is also increased when a user reuses their password elsewhere. Thus, when there’s a data breach elsewhere, it exposes the victim’s password when hackers attempt to utilize it elsewhere. The defense against this is to use secure hard to guess passwords, bolstered by app-based 2FA, and to not reuse passwords; use a password manager instead.
But an attacker doesn’t need to obtain a victim’s password to obtain access to an exchange account. If a hacker has been able to breach a victim’s email account first, perhaps also through a password breach or a SIM swap, they can use control of that email to reset the exchange account password. Even if a user has 2FA on their exchange account, that can also be breached in a variety of ways before the attacker would be able to withdraw funds. If the victim utilizes SMS 2FA, only a SIM Swap is necessary to have full access to the user’s exchange account.
If the victim uses Google Authenticator or Authy, the hacker may be able to find the backup codes on the email or backup cloud storage. Furthermore, Authy itself can be breached via a SIM Swap when not set up securely.
Thus it’s important to remember that the security of one’s email account (along with the ‘recovery options’) is just as important, if not more important than the exchange accounts themselves. It’s critical to use app-based 2FA or hardware-based 2FA like Yubikey and have it set up in a way so that you aren’t susceptible to being compromised in the event of a SIM Swap or password breach.
Exchange Reserve Hacks
The second type of attack is an attack on the reserves held by the cryptocurrency exchange itself whereby the hacker targets cryptocurrency assets which the exchange holds custody to itself.
These attacks can and do result in losses of hundreds of millions of dollars in each instance in some cases. After the hack, while a customers ‘account’ may show a ‘balance’ still, the reality is the exchange won’t actually have the assets to back up the ‘balance’ or liability to the user. The exchange is thus insolvent and can’t actually pay out its liabilities to customers (they could have been insolvent before the hack as well of course if they elected to borrow funds against customer assets).
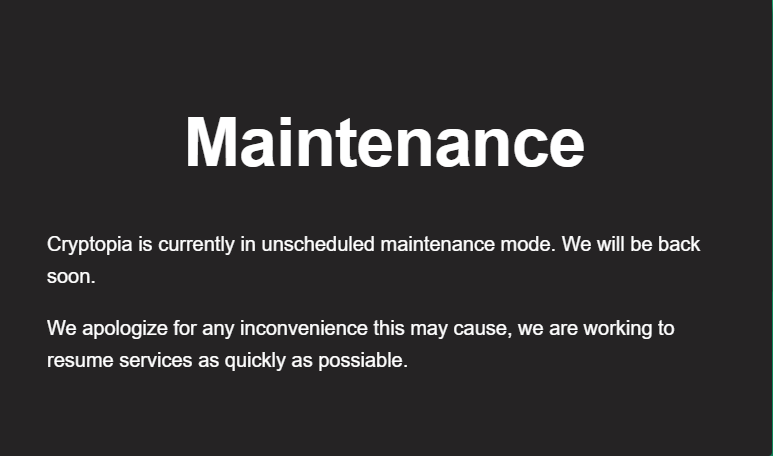
The message that appeared on Cryptopia before they publicly disclosed the hack
No amount of security one utilizes on their exchange account will prevent this type of hack. The only solution is to take custody of your own funds in your own wallet. Remember, not your keys, not your coins.
Hardware Wallet Attacks
A hardware wallet is only as good as how the user elects to store the seed phrase. We’ve seen plenty of people who have had their hardware wallets ‘hacked’ but in all the instances we’ve personally observed thus far, it’s always been a breach of the seed phrase where the user has been at fault, and thus not the fault of the hardware wallet itself.
There are a variety of techniques that have worked to a limited extent, at least in the past on hardware wallets, to include volt glitching and side-channels attacks but ultimately these are so rare and technically difficult to execute, that we have yet to come across someone who has been a victim of such an attack. A breach of the seed phrase is simply far, far more likely.
In the vast majority of instances, the seed phrase breach is going to be the fault of the user, but there have been instances of supply chain attacks on hardware wallets as well, as we’ve noted.
Conclusion
We haven’t listed all these security vulnerabilities to scare people. Hackers already know about them. Ultimately, your cryptocurrency will be far more secure once you’ve taken the time to understand these vulnerabilities, attack vectors, and the ways in which cryptocurrency is stolen. By understanding this, you can take measures to ensure you aren’t vulnerable through such attack vectors, although measures should be taken proportionally relative to the amount of cryptocurrency held.
That being said, security is also a double-edged sword here. A cryptocurrency user doesn’t want to be so secure that they end up losing the ability to access the funds themselves. Furthermore, users ought to have a place in place in the event of an untimely death for inheritance so that the funds aren’t lost forever. Importantly, the implementation of such a plan needs to avoid compromising the security of the funds prior to the death of the beneficial owner.

